50 Essential Cloud Computing Podcasts to Listen - 2020
50 Essential Cloud, DevOps and Security podcasts every cloud engineer, architect and security team should listen to.

Security is possibly the most important consideration for any organization storing data or hosting applications on public cloud infrastructure.
In this post, we’ll take a look at what AWS recommend you consider when approaching the subject of Security on the AWS platform. We’ll cover both the security considerations of the cloud itself and also what you can do within your own infrastructure to ensure your data is secure as explained in the 2021 AWS Security Fundamentals course.
AWS operates a shared responsibility model in that AWS assumes responsibility for the infrastructure that runs all of the services offered in AWS Cloud (Compute, Storage, Database etc)
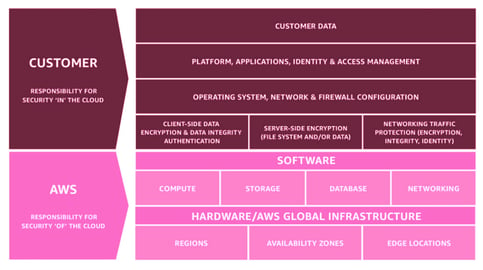
While you the customer are responsible for securing your data, networks, platforms, operating systems and all the resources you create using the AWS platform.
There are a number of core design principles that can strengthen your AWS security and can be used to guide discussions around your network and data security.
Enforce a strong identity foundation.
Segment access to your AWS resources based on a principle of least privilege. This entails the separation of roles and only permitting access to interact with resources that are appropriate for the role. Start with denying access to everything and grant access as needed.
Enable traceability.
Implement systems to monitor activity, trigger alerts and provide audit trails as changes are made to your infrastructure in real-time. Use logs and metrics to automate responses and trigger actions where necessary.
Set up security at all layers.
As well as setting up protection at the outer layer of your network, you should consider a defense-in-depth approach with multiple security measures.
Automate security best practices.
Utilise Automated software-based security tools to enforce controls. These can be defined and deployed as code via version controlled templates.
Protect data in-transit and at rest.
Classify your data based on the sensitivity of the data and then use encryption and access control to ensure only appropriate access is granted.
Prepare for security events.
Prepare for security events by creating an incident management process. This might entail running simulations and using tools to increase the detection and response to security breaches and the process to investigate and recover.
AWS provides security across its regions and availability zones, allowing you to leverage data centres close to your customers with some confidence. AWS security includes:
Data Center Security
All AWS data centers employ the principles of Least Privilege and limit physical access to areas within the data centres to both employees and contractors who have a legitimate reason for such access. Amazon employees whose job function does not warrant permanent access are treated like visitors and provided an escort while in the data center.
Professional security is employed at all physical data center locations which are protected via video surveillance, electronic intrusion detection, access control logs etc.
You would struggle to identify an AWS data center as they are typically housed in unsigned, nondescript buildings in locations unlikely to experience environmental disruptions due to fire, flood or seismic activity. The data centers have all the disaster mitigation and business continuity mechanisms in place like back up power systems and fire suppression equipment in constantly monitored hermetically sealed, climate controlled buildings.
AWS engages third-party certification to ensure it’s security and control environment is fit for purpose and provides a secure environment for customer data and workloads, many of which are publically available in the form of whitepapers. More detailed information can be provided under NDA due to the sensitive nature of security.
AWS Artifact is a free self service document portal where you can access AWS security and compliance reports like PCI (Payment Card Industry), Service Industry Control (SOC) and various other certifications and accreditations from around the globe.
Entry Points
Every operation on AWS makes an API call to perform the function. Whether you are making requests directly from the CLI, using one of the AWS SDK’s or performing operations through the Console, each service communicates via API calls. Identity and access management (IAM) is the security layer that authenticates and authorizes operations based on the IAM policies in place for the user and the service.
Users and Groups
When choosing to build on the AWS eco system, it pays to think about the types of users that will use your AWS infrastructure and how to group them in terms of applying permissions.
Following the least-privilege concept already discussed, you can assign access permissions for different groups of users based on their specific needs and restrict access to resources that they don’t necessarily need, after all there’s a big difference between read-only access and the ability to delete something.
IAM groups are collections of users who typically perform the same tasks and need differing degrees of access. You could for instance set up a “DevOps” group for role-based control so that permissions are assigned globally across the users belonging to this IAM group.
IAM has a number of levels and ways to control access.
The Password Policy is a set of rules that define the type of password an IAM user can set. From a security perspective it is best to enforce strong passwords and frequent change of passwords.
Multifactor Authentication is another layer that adds to your security. On top of your usual user name and password, a separate time limited code needs to be obtained from a registered MFA device. These devices can be physical hardware keyfob style devices or a smartphone ( iPhone / Android) application.
Each AWS user can also have 2 pairs of access keys generated to enable programmatic access to your infrastructure via digitally signed API calls.
In addition to user access keys, there are also Amazon EC2 keypairs that can be used to log in to EC2 instances although these do not provide traceability, as in who is using the keys to access an EC2 instance. If frequently accessed, AWS recommends that EC2 instances be part of a Directory domain like Active Directory or LDAP to enable visibility of what users are logging your EC2 instances.
In short, it is important to implement strong authentication methods like Active Directory integration, SAML, MFA and rotating passwords frequently as well as structuring authorisation permissions so that users can only access and execute on the bare minimum of resources and data required to do their job.
AWS provides a number of services for IAM (Identity & Access Management)
AWS Secrets Manager
AWS Secrets Manager is designed to centrally manage secrets used to access resources on AWS, on-premises, and third-party services. Secrets can be database credentials, passwords, third-party API keys, and even arbitrary plain text.
Secrets Manager enables you to replace hard-coded credentials in your code with an API call to Secrets Manager to retrieve the secret programmatically.
You can also configure Secrets Manager to automatically rotate the secret for you according to a schedule that you specify.
AWS SSO (Single Sign On)
AWS SSO is a cloud SSO service that allows for the central management of access to multiple AWS accounts and business applications.
SSO enables users to sign in to a user portal with their existing corporate credentials and access all of their assigned accounts and applications from one place.
AWS SSO includes built-in Security Asserted Markup Language (SAML) integrations to many business applications.
AWS SSO may be integrated with Microsoft Active Directory, which means your team can sign in to your AWS SSO user portal using their corporate Active Directory credentials.
AWS Security Token Service (STS)
If you need to give temporary access to IAM users who may be performing a different role or need temporary access for a specific task, STS enables you to create limited privilege temporary credentials.
AWS Directory Service
AWS Directory Service for Microsoft Active Directory (AWS Managed Microsoft AD) allows you to control your domain workloads and AWS resources using managed AD in the AWS cloud. This is built on actual MS AD but does not require connection or synchronization from your existing on-prem Active Directory.
AWS Organizations
You can centrally manage and enforce policies for multiple AWS accounts using AWS Organizations. You essentially group multiple accounts into organizational units and use service control policies that are applied across the accounts in the organization.
AWS Cognito
You can also bring user and access control to your mobile and web applications using Amazon Cognito. In cognito, you can define roles with certain resource access permissions and then map users to the roles.
Cognito manages a user pool (directory) that manages tokens received from SSO, SAML and AWS log ins and issues tokens that can be used to retrieve IAM credentials and policies to enable your apps to access AWS resources without having to embed long term AWS IAM credentials within your app.
As part of a well designed governance framework, your organization should have the ability to identify suspicious activity that could pose a security risk. AWS suggests a number of approaches to monitor and detect such activity.
AWS CloudTrail
As already mentioned, all operations conducted in the AWS environment are achieved using API calls, whether from the console, CLI or various SDKs AWS provide.
AWS Cloudtrail records API calls made on your account. The resulting logs allow you to inspect changes made to your AWS resources, view changes that may have caused unexpected network behavior and to troubleshoot operational issues.
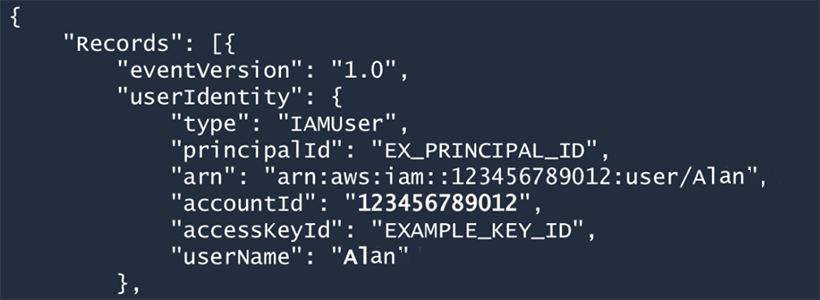
In this example log, we can see a user named Alan triggered a loggable event.
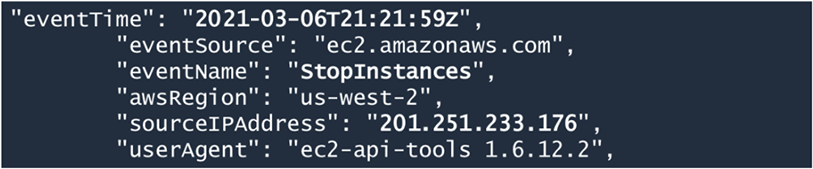
Scrolling on through the log entry we can establish Alan’s IP address, the event name or action performed ie Stop Instance and the source of the command which in this case is the AWS CLI
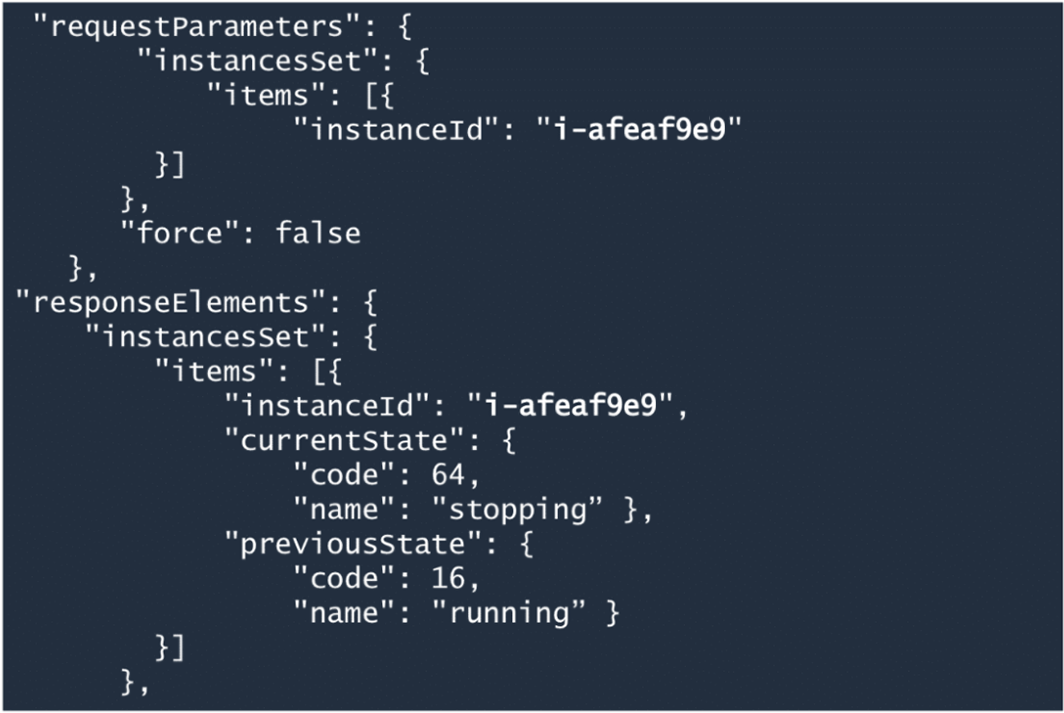
And finally we can see the EC2 instance ID and the state change. So in this case the response indicates the StopInstance call was successful.
Capturing and storing your API call logs is a great first step. To provide forensic auditable documentation it is a good idea to copy your logs to a separate secure AWS account that no users in the source account have access to. And likewise, no users in the target account should have access to the source account.
This ensures that no person, even with the highest admin permissions can manipulate evidence should the network logs be subjected to forensic analysis.
Amazon Cloudwatch
While logs are great and all, the downside is that you need to jump in and have some idea of what you are looking for. Whether it’s changes to a resource status or the creation of removal of instances, it is far better to be alerted as the changes happen rather than stumbling across them in the logs.
Cloudwatch is a service that will monitor your infrastructure in real-time and trigger alerts and remedial action operations in response. A cloudwatch alarm can monitor metrics and when thresholds are exceeded can trigger Lambda recovery actions and also notify subscribers via Amazon SNS so multiple team members can investigate and respond if necessary.
Other Monitoring Opportunities
S3 Buckets can be monitored using Server Access Logs
Elastic Load Balancers (ELBs) store access logs that capture IP addresses, server responses and latencies allowing you to analyze traffic patterns.
VPC Flow Logs capture details about the IP traffic ingress / egress through your network interfaces and subnets.
Amazon Guard Duty is a Machine Learning service that continuously monitors your infrastructure for threats and identifies suspected attacks via integrated threat intelligence feeds. Guard duty will detect unusual access activity, suspicious API calls or unauthorized deployments that may indicate your account has been compromised.
AWS Trusted Advisor is a service that reports on your infrastructure’s compliance with AWS best practices. The reporting module in Hava.io includes a AWS compliance report based on trusted advisor principles and will very often highlight security configuration issues.
AWS Security Hub gathers a lot of the higher priority security alerts into a single dashboard that can include data from multiple AWS accounts.
AWS Config is a service that monitors and assesses your AWS environments and detects non-compliance issues. You can enable several default pre-built rules as well as configure your own to ensure your company security policies are adhered to. This could include things like insisting all EBS volumes are encrypted or all your S3 buckets are set to private.
Protecting your systems and data from unauthorized or unintended access is the number one priority when designing your infrastructure.
AWS Virtual Private Networks (VPC) allows you to isolate your AWS resources in the cloud by creating virtual networks and subnets that mimic traditional on prem networks.
The way you configure access to your infrastructure determines who can access your systems and AWS VPCs provide a number of security components.
In a typical EC2 setup, the instance is protected by
Subnet Routing - this allows you to group resources into a subnet. The subnet can have IPv4 and/or IPv6 addresses and can be configured to be accessible via the internet (or not)
Network Access Control Lists (ACLs) add a further layer of security by acting as a gatekeeper. By default your VPC comes with an ACL that allows all inbound and outbound traffic. You need to configure your ACL with ALLOW or DENY rules for specific IP addresses, protocols and ports to control who gets in.
Security Groups - A security group contains a set of rules for inbound and outbound traffic. When you create a new instance in a VPC you must nominate which security group it belongs to. No inbound traffic will flow until the inbound rules are defined in the security group which can be based on IP Protocol, service ports and source/destination IP address.
AWS Firewall Manager - a security management service that allows you to centrally manage WAF rules across accounts and applications. You can use AWS WAF instances to ensure new applications, resources and VPCs are subject to a common set of security rules.
Just because you are building in the cloud doesn’t mean you can ignore the software protocols that apply to on-prem or data center hardware. Operating system patches and anti-virus definitions for instance still need to be kept up to date.
AWS Systems Manager is a service that can help automate patching and OS maintenance at scale.
Inspector is an automated security assessment service that monitors and suggests improvements to applications deployed on AWS. Findings are detailed by level of severity. On top of alerts, inspector can also initiate corrective actions.
For example, Inspector could run assessments of a group of EC2 Instances. Using SNS, alerts are sent to the administrator or subscribers to the SNS service and an alert then triggers a Lambda function to analyse the findings and run corrective patch operations on the problem EC2 instances.
There are several consideration surrounding the protection of data (via encryption) when using AWS. You need to consider the protection of data at rest namely how the data stored is encrypted. This is determined by who is providing and managing the encryption keys and whether the encryption takes place on the client or server side.
You also need to consider the protection of data in transit. Selecting the most appropriate protocols for traffic flow ensures the data integrity as you move data.
AWS provides several protocols for protecting data in transit
HTTPS endpoints using TLS for end-to-end encryption when using AWS APIs
TLS - AWS can generate, manage and deploy public and private certificates for TLS encryption of web based applications
IPsec with VPN connectivity into AWS
AWS also provides some other services to help with security strategies.
S3 Glacier Lock Policy - Glacier is an archive storage solution for infrequently accessed data which is stored in archives within vaults. Each vault can have a vault lock policy applied.
AWS Cloud HSM - is a hardware security module that generates and stores encryption keys for use with HSM instances on AWS cloud.
AWS Certificate Manager - creates and manages public SSL/TLS certificates for AWS based applications and websites. Private X.509 SSL/TLS certificates can also be issued to help track and identify computers, services, applications and other devices internally.
Amazon Macie - Amazon Macie is a fully managed data security and data privacy service that uses machine learning and pattern matching to discover and protect your sensitive data in AWS.
Macie automatically provides an inventory of Amazon S3 buckets including a list of unencrypted buckets, publicly accessible buckets, and buckets shared with AWS accounts outside those you have defined in AWS Organizations. Then, Macie applies machine learning and pattern matching techniques to the buckets you select to identify and alert you to sensitive data, such as personally identifiable information (PII).
When an incident is detected, you need to act as fast as possible to isolate and investigate the resources impacted by the event.
With physical hardware in your own on prem network or data centre this often involves physically isolating hardware devices or pulling the plug on equipment to circumvent the attack.
With cloud computing you have a number of options that provide more convenient mitigation actions. You could for example isolate an instance by changing it’s security group with a single command line API call
Investigating the state of data volumes may require taking a snapshot of a disk image for further forensic analysis. Amazon EBS snapshots simplify this process.
Hava’s versioning allows you to view snapshots of your network configuration at any point in time. As changes are detected, new network topology diagrams are generated and the superseded diagrams are placed into version history, including all the attributes and metadata pertaining to the resources in the environment. This makes it easy to open an interactive historical representation of your network and investigate all the settings.
AWS CloudFormation
AWS cloudformation can be used to quickly replicate environments into a new isolated environment where deeper forensic analysis can be performed in isolation from your production environment. Forensic teams can then identify the cause or vulnerability that lead to the incident.
AWS Step Functions
AWS Step Functions is a serverless function orchestrator that makes it easy to sequence AWS Lambda functions and multiple AWS services into business-critical applications.
Step Functions can be used to rebuild or recover compromised instances
Distributed denial of service attacks are becoming more commonplace and AWS provide a number of services to prepare and mitigate DDoS attacks on your AWS environments.
AWS Edge locations can provide an additional layer of infrastructure that AWS provide to help weather DDoS activity. The edge locations are physical data centers separate from availability zones. As data activity increases, data is copied to edge locations to be closer to your users for performance and reduced latency which provides the opportunity to resolve threats at the edge location away from your actual data and application location.
There are several AWS services that allow you to establish a security perimeter at the edge to guard against various forms of DDoS attacks.
Amazon Route 53 - this DNS service is primarily used to route traffic to your web applications. The advanced features of Route 53 allow you to control traffic flow, implement latency based routing, Geo DNS and health check monitoring. The nature of the service provides a global surface area capable of absorbing large amounts of traffic experienced during DDoS attacks.
Amazon Cloudfront - This CDN service is used to optimize the delivery of data including your entire website to end users. The service only accepts HTTPS and well-formed HTTP connections, which will prevent many common forms of DDoS attacks. This gives your application a fighting chance to deliver data during larger intense attacks.
AWS Shield - This is a dedicated managed service that offers always-on protection for web apps running on AWS from DDoS. AWS Shield will deploy inline mitigations that will reduce application downtime and latency
AWS WAF - Web application firewall helps protect your applications from web exploits that drain resources, affect the availability of your applications or compromise security. WAF allows you to allow or block traffic based on custom web security rules and access control lists.
There is a huge emphasis placed on security by AWS and a vast selection of tools and methodologies involved and I suspect we have barely scratched the surface in this post.
Security is also a major focus here at Hava. As well as visualising network topology diagrams for AWS environments we also automatically produce a Security Group diagram that details all the detected security groups for each VPC.
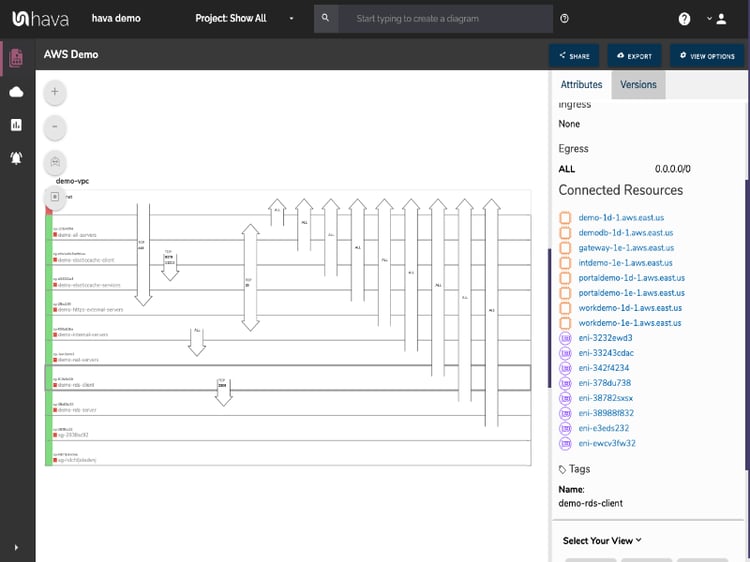
Overlaid on top of the security groups are the ports and traffic flow and as with all Hava diagrams, this view is interactive which enables you to click on security groups and see all the connected resources, IP addresses and port ingress/egress information.
This visualization of your AWS security can allow your security team to quickly spot misconfigurations and what security groups are controlling access to without tedious trawling through hundreds of console settings.

If you want to check out what your security looks like visualized, as well as your what your cloud architecture looks like as discovered by the Hava AWS Diagram Creator, please take a free trial. Learn more below.
50 Essential Cloud, DevOps and Security podcasts every cloud engineer, architect and security team should listen to.
How many ways can a simple security view diagram help enhance your cloud security? In this post we take a look.
Connecting Hava to your AWS and Azure accounts generates interactive security diagrams your team can use to visualise and review your cloud security...