
As part of our ongoing quest to help you understand what your cloud infrastructure and security posture looks like through easy to understand diagrams and visualisations, several enhancements to the current security view diagrams have been released that deliver even more clarity to potentially complex visualisations.
Protocol Names
The first enhancement is the addition of protocol names to tcp port numbers on the traffic arrows. This is designed to indicate how and why a specific port number is being used and saves you having to look up what an open port on your security diagram is normally used for.
The protocol names are shown in the attribute pane to the right of the security view diagram once a specific rule arrow is selected. In the below example the arrow depicting traffic ingress from the internet and being delivered to a security group shows ports 443, 5601 and 9200. You probably recognise port 443 is HTTPS, but what about the other two.
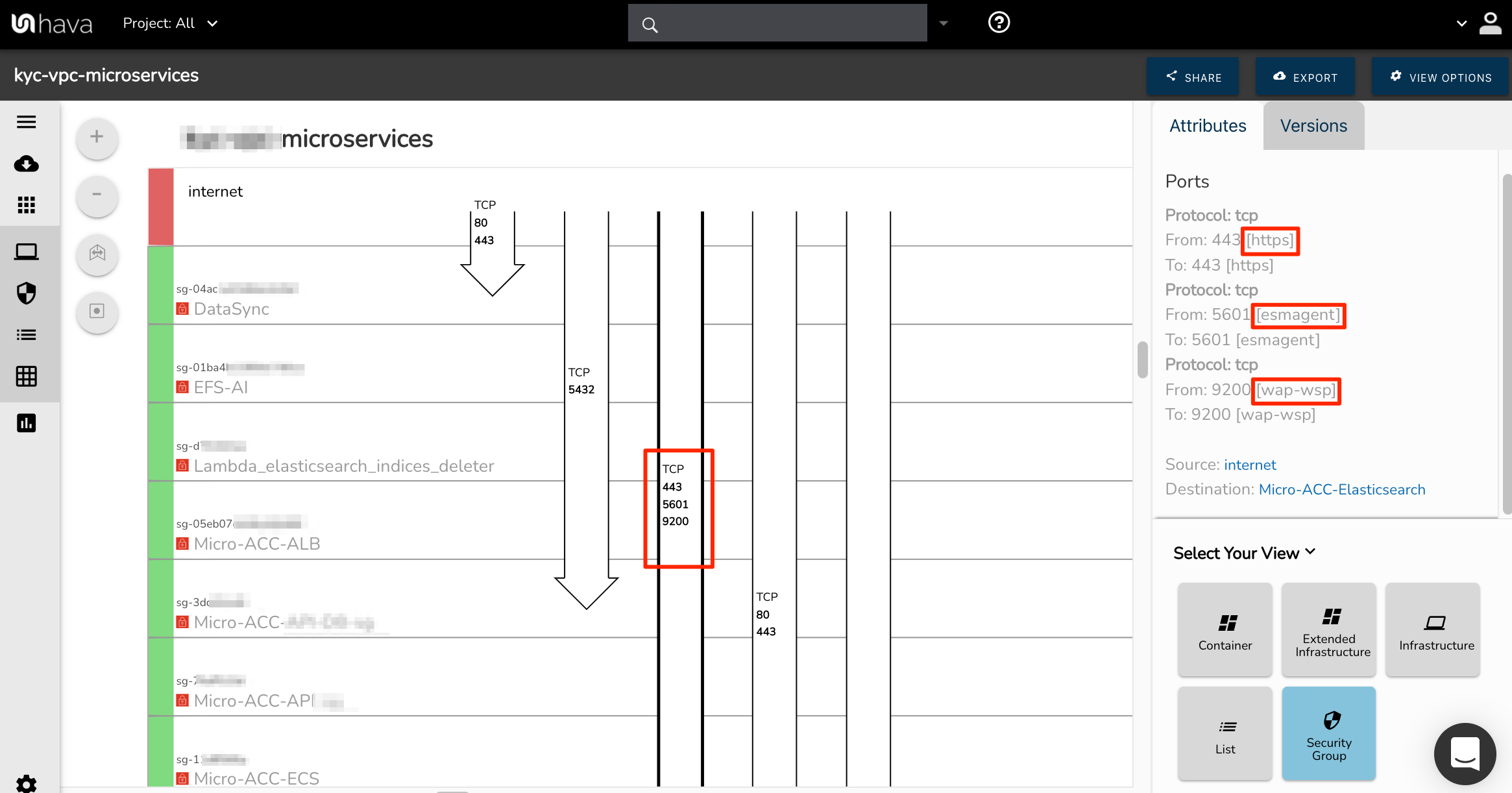
At a glance we can see port 5601 is used by esmagent and port 9200 is wap-wsp without having to go and look them up.
Segmented Security Groups
Hava's ability to consolidate multiple VPCs on the same diagram, even if they are from multiple cloud providers or AWS accounts can in some circumstances cause some confusion or lack of clear delineation when viewing a multi network security diagram,
To solve this potential problem the security view diagram has been enhanced to segment networks on the view instead of listing all the security groups in one block.
If we use the Hava search function to return two VPCs on the same diagram, the resulting diagram places the two VPCs side by side:
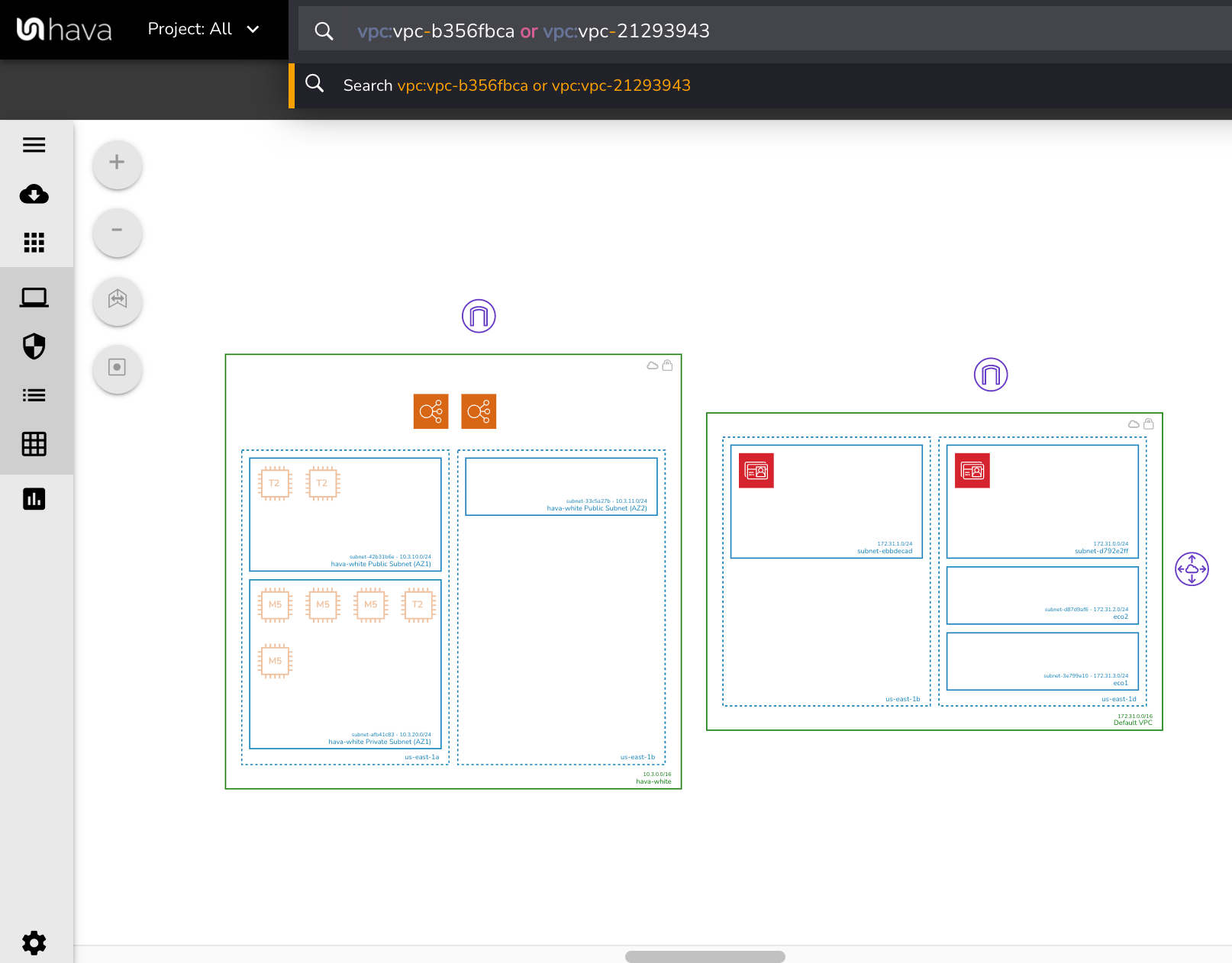
The two VPCs displayed in this example are named "hava-white" and "default vpc".
When we open the security view, you can now see the security groups for each VPC separated into two blocks, instead of being merged as in previous versions.
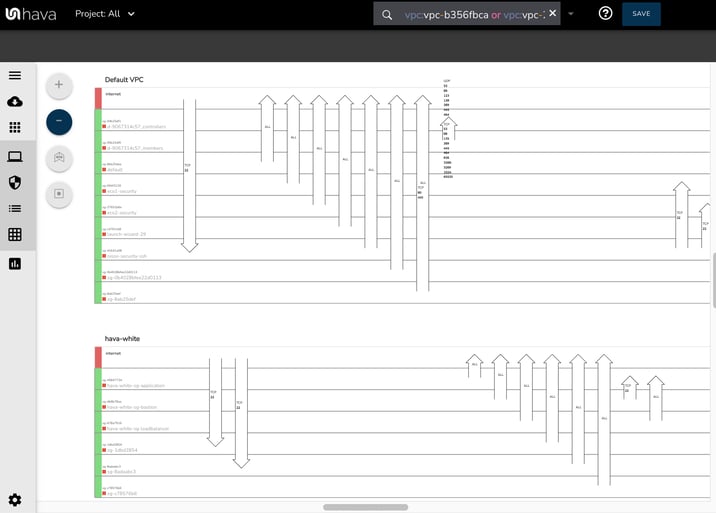
Now the security groups are clearly segmented into the different networks on the diagram.
Source and Destination in Arrow Metadata.
When you are inspecting a security view diagram that has hundreds of traffic arrows you will often be required to scroll to the right and then scroll up or down to find the security group ingress source and then scroll again to find the destination. On large diagrams that could make identifying the source and destination security group names a little tedious.
To solve this issue, the source and destination security groups are displayed in the attribute pane when a traffic arrow is selected on the interactive diagram.
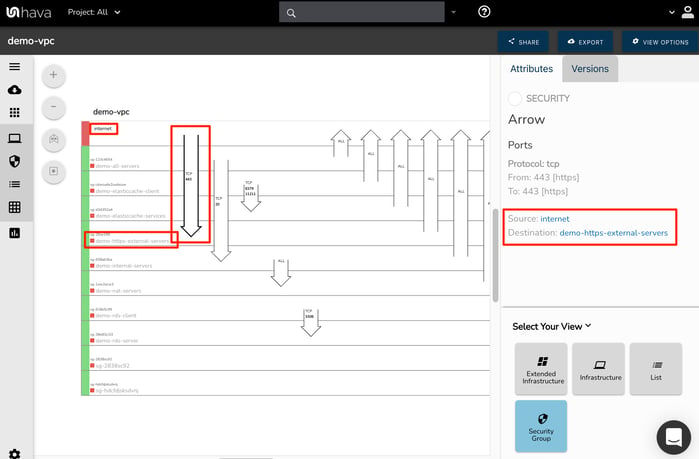
Suppress default "ALL" rules.
On AWS security views, there can be a significant number of default "ALL" ports protocols created when security groups are provisioned. When you are looking for the configurations where explicit port rules have been configured the ability to hide the default "all" arrows can be useful.
As a default, the "ALL" rules are shown:
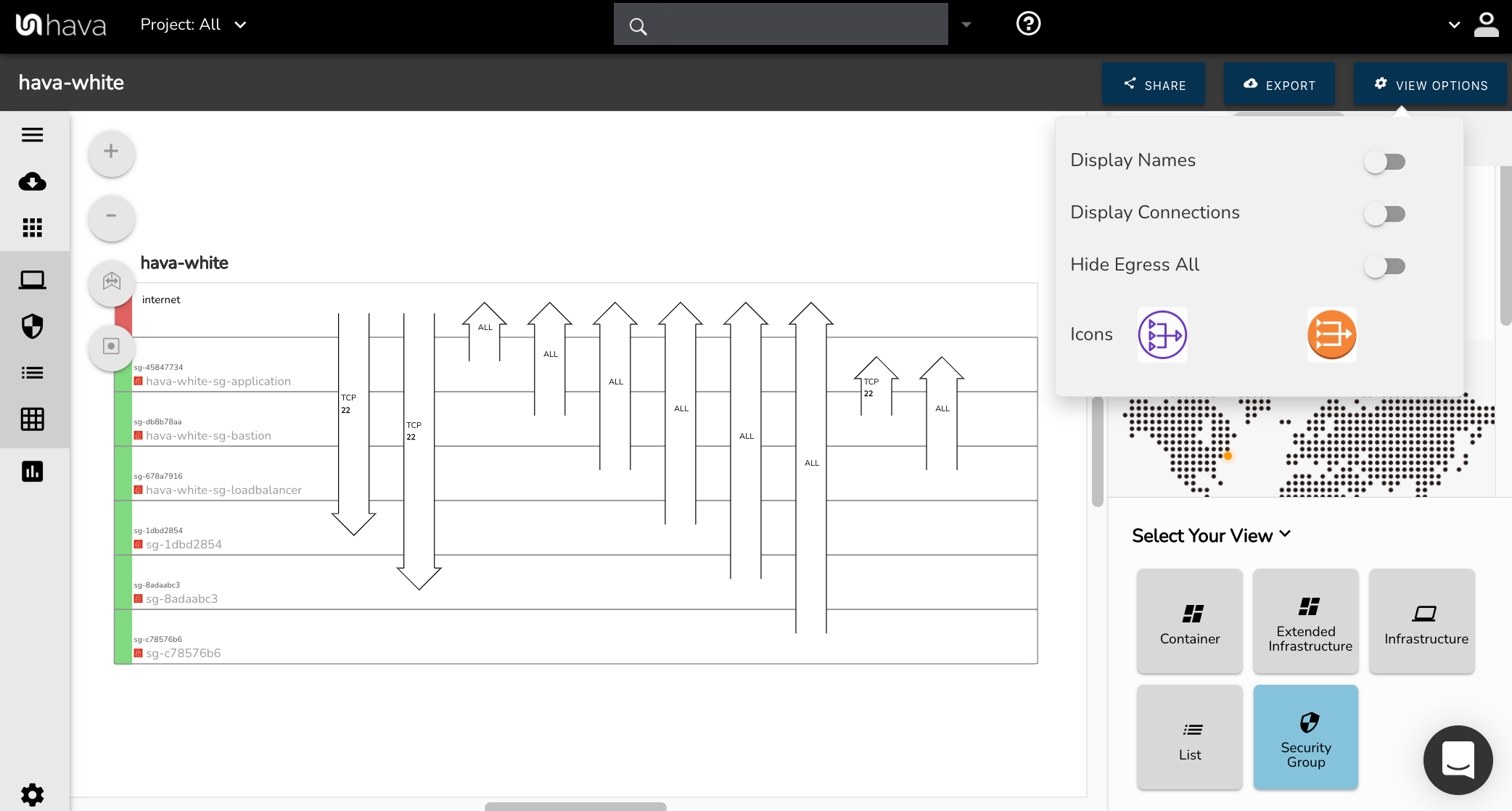
Under the view options on the top right toolbar, you can now hide the default "All" egress arrows by sliding the toggle switch on.
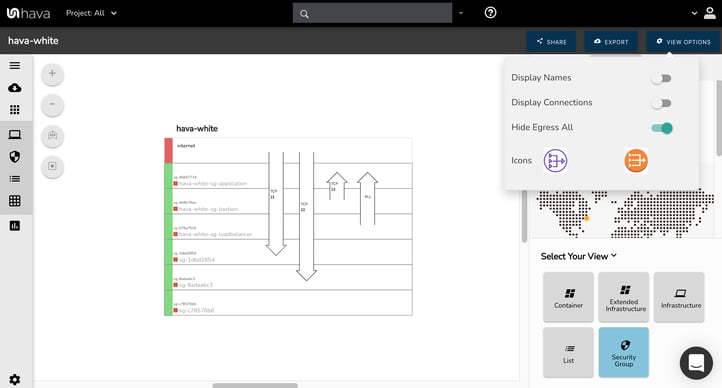
As you can see, this delivers you a much cleaner security group diagram, allowing you to pinpoint the rules with explicit ports configured.
So that's a run through the latest refinements to the security view and we hope it adds a little more clarity and utility to this unique and extremely useful tool to help your security team visualise your network security.
If you are already using Hava to auto generate your cloud infrastructure and security diagrams, these changes are live and you should see them already in your security views.

If you are not a Hava user, you can see exactly what security groups and ports you have open in your AWS and Azure environments by taking a 14 day free trial and adding Hava to your cloud engineering toolkit.